In the advanced digital world, information security is fundamental for protecting sensitive and significant data. To safeguard transactions, customer data, and trade secrets, data security, and protection plans are now essential for organizations and businesses. A company’s finances, in particular, could suffer catastrophically if data is misused. Along these lines, a ton of organizations choose to utilize and maintain Access Control such as Mandatory Access Control.
What is Access Control?
Access Control is a fundamental network protection idea used to implement secure data. It manages directing, making due, and controlling access consents of people to explicit assets or data inside a data set.
The essential point of Access Control is to anticipate undesirable access by guaranteeing that the main people with the approvals are allowed passage into the framework.
The key parts that make up Access Control include Access Control Models, Authentication, Authorization, and Access Policies.
In the realm of online protection, the idea of Access Control has been taken on to control and screen grants to information, applications, assets, and organizations in the computerized space, consequently authorizing security and protection.
What is the meaning of Mandatory Access Control (MAC)?
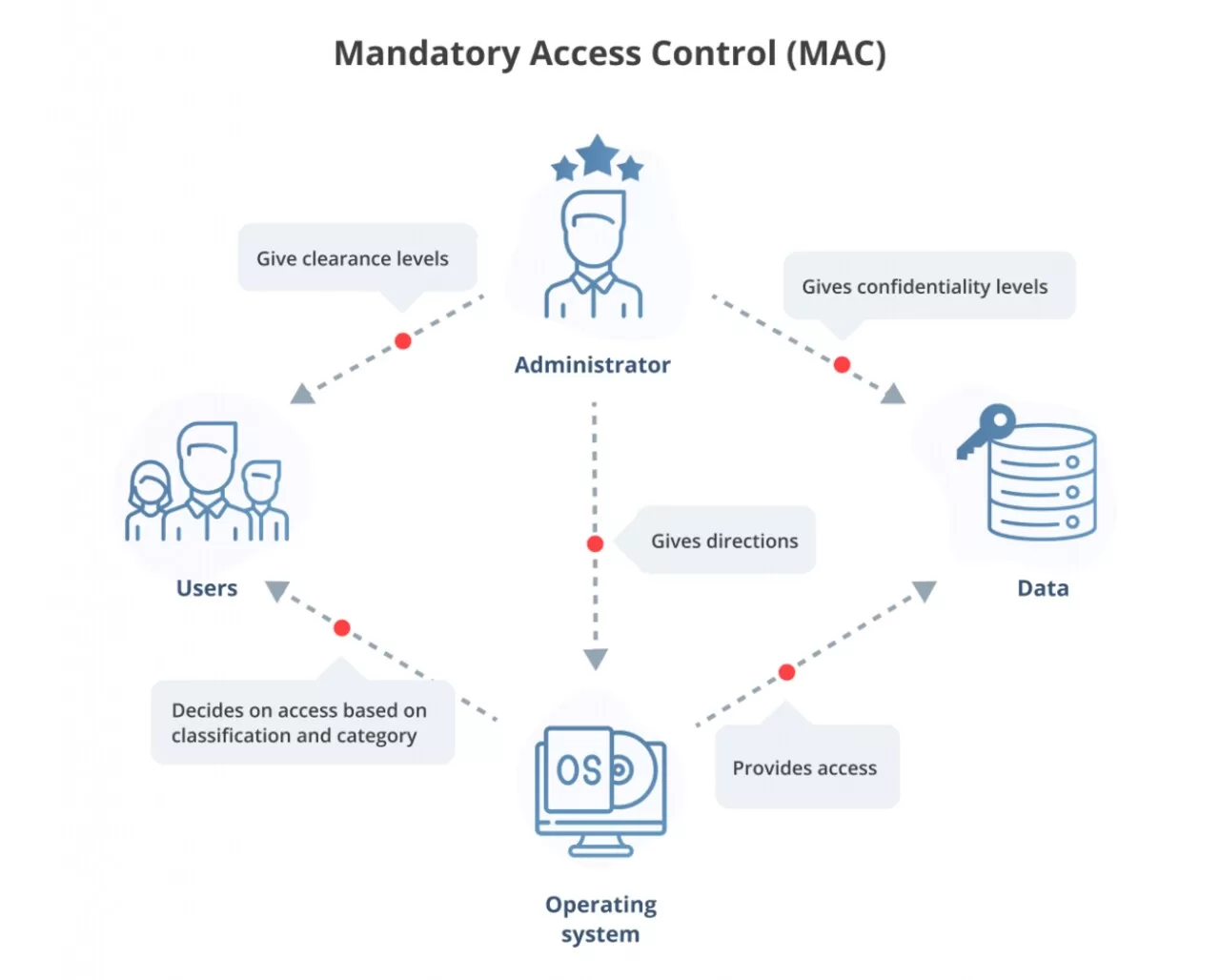
Mandatory Access Control (MAC) is a framework that allows an association to conclude who can and can’t get to private data. The order design that supports MAC’s activity separates it from different frameworks.
The entire team must be classified according to their roles, responsibilities, and access to information under this system.
That’s what to guarantee, the organization should focus on precisely arranging the data progression. The association should just be done once, and updates would possibly be required assuming the position or job changed afterward.
Access is organized under MAC so a representative who approaches more significant level information can likewise get information accessible to their lower-level positions.
In simple words, it’s like a data stream diagram where the individual in the center can get information at the ground level yet not at more significant levels.
It is common practice in workplaces where MAC systems are to be used to classify information flow into distinct categories. Such as top-secret, confidential, ground-level, and secret.
Every system that a person could be using has been granted advance access as a part of cyber security Mandatory Access Control.
Mandatory Access Control Vs Discretionary Access Control:
Discretionary Access Control, or DAC, is a network protection model that spots Access Control experts in the asset proprietor’s hands. Dissimilar to MAC, DAC gives clients and asset proprietors access to privileges for their assets.
This implies that the asset proprietor will conclude who can get specific information and who can’t. The Unix operating system is an illustration of DAC.
The crucial objective of DAC is to guarantee and authorize security by giving over power and Access Control to the clients and asset proprietors as opposed to the frameworks.
The most important aspect of controlling resource access is the main distinction between Discretionary and Mandatory Access Control.
In Discretionary Access Control, access is constrained by the asset clients, while in required Access Control, access is constrained by the framework.
What are the pros and cons of Mandatory Access Control?
Due to the extensive use of MAC across various industries, a system that can protect sensitive data without ongoing oversight is needed. Especially in fields such as government agencies, the armed forces, healthcare, banking, and engineering projects, among others. In addition to its many advantages, MAC also has many disadvantages. Below is a list of a few of them:
Pros:
- With MAC, one should rest assured that their most secret information is very much secured and rules out any spillage.
- Whenever information is set in a class it can’t be de-sorted by anybody other than the head executive. This makes the entire framework brought together and heavily influenced by just a single power.
- Information is set physically by a chairman. Nobody other than the administrator can make changes in the classification or rundown of clients’ gets to any class. It tends to be refreshed simply by the administrator.
Cons:
- If the MAC is not set up properly, working will become chaotic. This is because MAC makes it impossible for anyone to share information with coworkers within the same organization.
- It requires standard refreshing when new information is added or old information is erased. The organization is expected to place a few thoughts into the MAC framework and leg tendon rundown from time to time.
- The MAC framework isn’t functionally adaptable. It’s anything but a simple undertaking to first inform all information and make an upper leg tendon that will not cause any difficulty later.
Conclusion:
MAC is the most reliable framework because it is suggested in workplaces where exceptionally classified information is required to have been safeguarded and not in any confidential workplaces. Where a less solid framework would be sufficient.
In a quickly developing computerized scene, having a vigorous information procedure around Access Control is fundamental to guaranteeing information security.
Different organizations represent considerable authority in information benefits that enable organizations to come to informed conclusions about Access Control techniques and innovation arrangements.
Whether you’re inclined towards the client-characterized adaptability of DAC or the concentrated power of MAC, our specialists are here to direct you.
Furthermore, your association can unify its data and investigation, making it more
straightforward to deal with the entrance control for each partner, including staff, clients, merchants, accomplices, and so on.
Frequently Asked Questions:
What is mandatory access control?
Mandatory access control is a technique for restricting access to assets in light of the responsiveness of the data that the asset contains and the approval of the client to get to data with that degree of awareness.
Who grants access in a mandatory access control?
These principles are set by a director and authorized by the framework. Confining the singular capacity for asset proprietors to give or deny admittance to record objects.
Are the mandatory access control methods used to control access?
In short, yes. It is a method for confining admittance to framework assets given the awareness of the data contained in the framework asset and the conventional approval.
Which of the following describes mandatory access control (MAC)?
Mandatory Access Control is described by an authorized access model comprising safety surveillance levels or divisions.